Hello to all! I am a newbie at ZT and I couldn’t find the answer on the manual, wiki or posts.
That said, here’s an ASCII diagram of what I have:
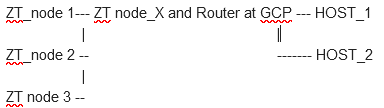
ZT Net: 172.30.0.0/16
HOST Net: 192.168.0.0/16
And so on and so forth.
With the default ZT rules I can perfectly reach from a ZT node with IP: 172.30.100.20 to a host BEHIND the ZT Router with IP 192.168.0.1
The problem is that I want to LIMIT the ports that the ZT nodes can reach on the HOST network. Per de documentation and a friend advice, of course I can define TAGs and use them to define traffic between the ZT nodes. The problem is that my destination hosts are BEHIND a ZT node.
Is it possible to create rules that will apply to hosts BEHIND the ZT node that is working as router?
Here’s the rules I created that of course does not work.
I have defined POD with the TAG 300 but the destination host is BEHIND IT!
What would be the rules I need to create for this scenario?
Your help is really appreciated!
Regards,
David.
Rules start here:
tag class
id 2 # arbitrary, but must be unique
enum 100 pods # has no meaning to filter, but used in UI to offer a selection
enum 200 student
enum 300 teacher
default student;
drop
not ethertype ipv4
and not ethertype arp
;
drop not ipprotocol tcp; # Cleanup rule to only allow TCP that I need.
accept dport 3389 and tseq class 200 and treq class 100; # RDP Student to PODs
accept dport 3389 and tseq class 300 and treq class 100; # RDP Teacher to PODs
accept dport 80 and tseq class 200 and treq class 100; # HTTP Student to PODs
accept dport 80 and tseq class 300 and treq class 100; # HTTP Teacher to PODs
accept dport 22 and tseq class 300 and treq class 100; # SSH Teacher to PODs
drop chr tcp_syn and not chr tcp_ack; # Cleanup TCP states.
`# Accept anything else. This is required since default is 'drop'.`
accept;