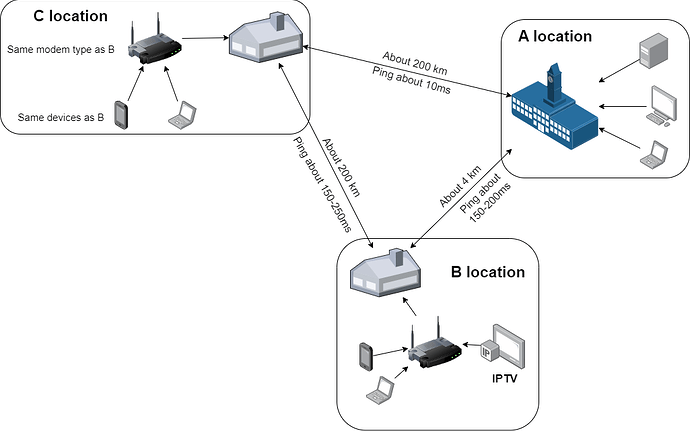
I deployed Zerotier in 3 different geographical locations, temporarily called A, B, C respectively. Locations A and B are in the same city, about 4 km apart. Every device at location B when pinging to A and vice versa is about 150-200ms, file transfer speed is about 10mbps or less. At first I thought everything like that was normal, until I brought my laptop home in position C and remotely controlled the devices in position A. It was strange that when I tested the ping it was only about 10-20ms, file transfer speed up to 100mbps. I checked the peer with zerotier-cli and found that devices at A and C both connect “DIRECT” but B to other locations and vice versa all “RELAY”.
All 3 locations use the same service provider and the same price. Network equipment at points B and C are the same. The test equipment for measuring is the same (I brought my laptop and smartphone from B to C).
From the above, I think the problem is not with the device or the installation, but with the network at location B. More precisely, it may be because the service provider has blocked something on the network at location B. I tried searching online and every keyword I noticed was “NAT strict”. But I’m still not sure if it’s due to it and how to tell the service provider to unblock it. In addition, at location B, using the IPTV service of the network service provider, they said that the IPTV line and the regular internet connection are two different lines. However, when installing, I saw that they only plugged an optical cable into a Modem (which also functions as a router and also broadcasts wifi) and then connected to the TV and other devices via LAN. I don’t know if that has anything to do with it? I don’t have much background in networking so please help me figure out the problem and how to fix it.
Diagram of locations